Contents
Global Settings for L4xNAT Farm Profile
The L4xNAT farm profile creates LSLB farms that operate at layer 4 with exceptional performance, offering more simultaneous connections compared to load balancer cores at layer 7. The improved performance at layer 4 offsets the advanced content handling capabilities of a layer 7 farm profile.
Unlike layer 7 farm profiles that only support ports 80 and 443, the L4xNAT farm profile utilizes multiple ports, including port ranges.
This section provides a detailed explanation of the required commands for configuring an L4xNAT farm profile. We highly recommend using Farmguardian in conjunction with this profile to monitor the status of each backend configured on the farm since this profile does not include any built-in health check functionality.
Take note of the Status indicator and the Actions section in the upper right corner. The Actions available in this section allow you to perform operations such as Restarting, Starting, or Stopping the farm.
These are the Status color indicators and their meanings:
- Green: Means UP. The farm is running and all backends are UP or the redirect is configured.
- Red: Means DOWN. The farm has stopped.
- Black: Means CRITICAL. The farm is UP but there is no backend available, or all backends are in maintenance mode.
- Blue: Means PROBLEM. The farm is running but at least one backend is down.
- Orange: Means MAINTENANCE. The farm is running but at least one backend is in maintenance mode.
These color codes are the same all over the graphical user interface. Find an in-depth explanation about these color codes in the LSLB Farms Section.
Basic configuration
These are the parameters for the L4xNAT profile.
Name. A label that easily identifies a farm service. To change this value, you must stop the farm first. Ensure that the new farm name isn’t already in use or else an error message will appear.
Virtual IP and Port. These specify the address and port on which the farm will listen internally within the appliance. If you wish to modify these fields, ensure that the new virtual IP and virtual Ports are not currently in use by another farm. Once you have made the changes, save them, and the farm service will automatically restart.
To select a single port or a range of virtual ports in the L4xNAT farm profile, a Protocol type is mandatory. In case the protocol is set to ALL, the farm will listen on all ports from the virtual IP. The virtual port will not be editable and will be set with an asterisk (*).
Once TCP, UDP, or any other protocol is selected, use it to specify a port, several ports, or port ranges.
Advanced configuration

Protocol Type. This field lists all the supported protocols on the load balancer. By default, the farm uses the TCP protocol.
- ALL. The farm will listen for inbound connections to the current virtual IP and port(s) over all protocols. If you selected this option, the virtual port will change to the default “*”, and you’ll not edit it. So, the farm will listen through all ports.
- TCP. Enabling this option allows the farm to listen for inbound TCP connections to the current virtual IP and port(s).
- UDP. Enabling this option allows the farm to listen for inbound UDP connections to the current virtual IP and port(s).
- SCTP. Enabling this option allows the farm to listen for inbound SCTP connections to the current virtual IP.
- SIP. Enabling this option allows the farm to listen for inbound UDP packets to the virtual IP and the default port, 5060. The farm will then parse the SIP headers of each packet to be correctly distributed to the backends.
- FTP. Enabling this option allows the farm to listen for inbound TCP connections to the current virtual IP and the default port, 21. The farm will then parse the FTP headers of each packet to be correctly distributed to the backends. Two modes are supported: The Active and the Passive mode.
- TFTP. Enabling this option allows the farm to listen for inbound UDP packets to the current virtual IP and the default port, 69. The farm will then parse the TFTP headers of each packet to be correctly distributed to the backends.
- PPTP. Enabling this option allows the farm to listen for inbound TCP connections to the current virtual IP and port. The farm will then parse the PPTP headers of each packet to be correctly distributed to the backends.
- SNMP. Enabling this option allows the farm to listen for inbound UDP packets to the current virtual IP and port. The farm will then parse the SNMP headers of each packet to be correctly distributed to the backends.
NAT Type. The NAT Type functionality within the appliance governs all the layer 4 operations. Choosing the appropriate option for your infrastructure will depend on the specific network architecture defined in your environment.
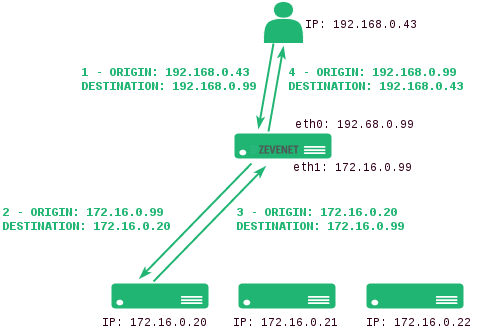
- NAT. The NAT mode or SNAT (source NAT) uses the farm’s Virtual IP as the source IP address to connect to the backend servers. Therefore, the backend servers shouldn’t know the original source IP address of a web client at TCP, UDP, or any other layer 4 protocol. This way, the backend responds to the load balancer, then the load balancer will respond to the client. This topology permits the deployment of a one-armed load balancer (load balancing with 1 network interface).
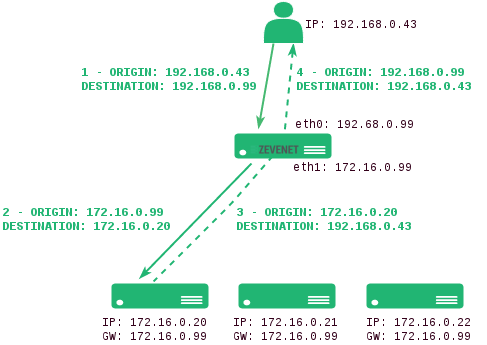
- DNAT. In DNAT (Destination NAT) mode, we shall use the client IP address to connect with a backend server. As a result, the backend will directly respond to the client IP. In this case, the load balancer IP should be configured as the backend’s default gateway, effectively separating the backend network from the client service network. This topology establishes transparency between clients and backends.
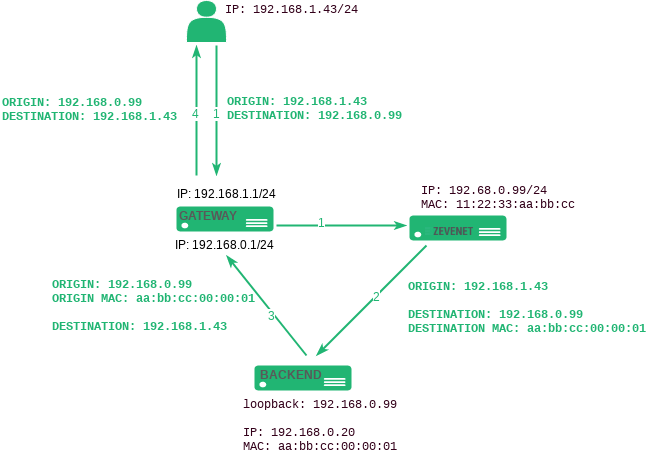
- DSR. In DSR mode, the client connects to the load balancer’s Virtual IP (VIP). The load balancer then alters the Destination MAC address by changing it to that of a backend server without changing any IP address. However, all backend servers must be on the same network as the load balancer. When a backend server receives and processes the request, it directly responds to the client, bypassing the load balancer.
Requirements for DSR:
- The VIP and backends must be in the same network
- The Virtual Port and the Backend Ports must be the same
- One must configure the backends loopback interfaces with the same IP address as the VIP configured in the load balancer and disable ARP in this interface
Linux backends
# ifconfig lo:0 192.168.0.99 netmask 255.255.255.255 -arp up
Disabling invalid ARP responses in the backend.
# echo 1 > /proc/sys/net/ipv4/conf/all/arp_ignore # echo 2 > /proc/sys/net/ipv4/conf/all/arp_announce
Windows backends
- Start->Settings->Control Panel->Network and Dial-up Connections.
- Right-click on your network adapter and click Properties
- Only Internet Protocol needs to be selected (remove the selection of “Client for MS Networks” and “File and Printer sharing”)
- TCP/IP Properties->enter IP address of the VIP in ZEVENET ADC farm. The default gateway is not required and the mask is 255.255.255.255
- Set Interface Metric to 254. This configuration is required to stop replying any ARP response to the VIP
- Press OK and save the changes.
First, configure the strong host security model to enable traffic reception from ZEVENET ADC on the NIC interface. Additionally, allow ZEVENET ADC to send and receive traffic through the default NIC interface. Open the command prompt as an administrator and execute the three provided commands.
netsh interface ipv4 set interface NIC weakhostreceive=enabled netsh interface ipv4 set interface loopback weakhostreceive=enabled netsh interface ipv4 set interface loopback weakhostsend=enabled
Note: Change the NIC and loopback to the default Interface Names of your Windows computer.
Stateless DNAT. With Stateless DNAT, the load balancer modifies the destination address to the backend address and passes it on without keeping track of any connection details. This approach reduces the burden on the system as it is implemented early in the data flow. It is most suitable for layer 4 protocols with heavy traffic and for protocols that are not focused on maintaining connections or streams, like RTP or SYSLOG UDP mode.
Logs. To save the details about the connections received on the farm, enable the Log command. This is only recommended for debugging or monitoring purposes because it will slow traffic handled by the load balancer.
Service settings
The service created in the L4 layer provides the following configuration options for managing the data paths and connection behaviors.
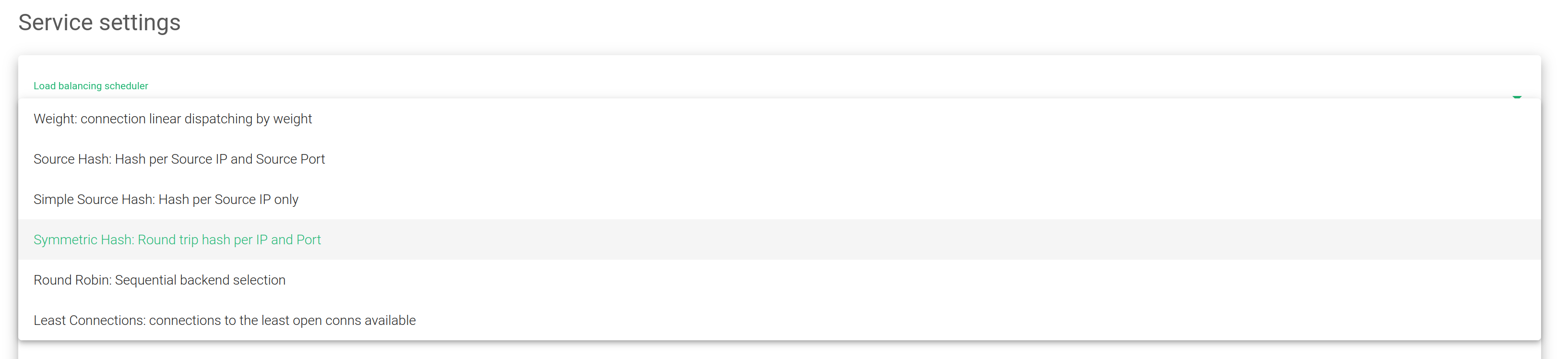
Load balancing scheduler. This field specifies the load balancing algorithm to be used for determining the backend server. By default, the load balancing algorithm will Weight: connection linear dispatching by weight
- Weight: connection linear dispatching by weight. Balances the connections depending on the weight value that has been assigned to each backend. The requests are delivered using a probabilistic algorithm using the defined weight.
- Source Hash: Hash per Source IP and Source Port. Balances the packets that match the same source IP and port to the same backend using a hash scheduler.
- Simple Source Hash: Hash per Source IP only. Balances the packets that match the same source IP to the same backend using a hash scheduler.
- Symmetric Hash: Round trip hash per IP and Port. Balances the packets that match the same source IP and port, and the destination IP and port. So, it could hash a connection in both ways (during inbound and outbound).
- Round Robin: Sequential backend selection. It balances each incoming connection to a backend, sequentially switching between backends.
- Least Connections: connection always to the least connection server. Selects the backend with the least number of active connections to ensure that the traffic load of the active requests is balanced with the traffic load of the most connected available real server.
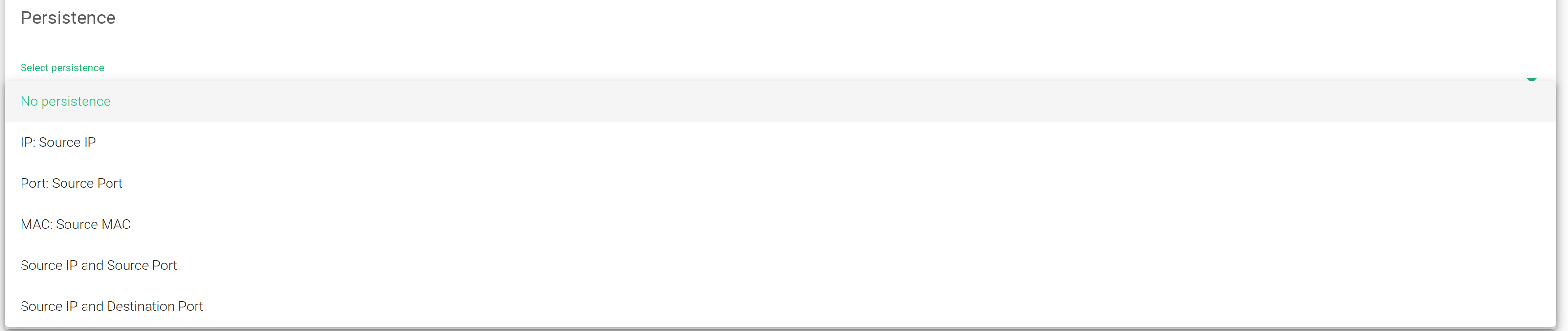
Persistence
Select persistence. This field determines persistence is to be used in the configured farm. By default, No persistence is used.
- No persistence. The farm will not use any persistence between the client and the backend.
- IP: Source IP. With this option, the farm will assign the same backend for each incoming connection depending on the source IP address only.
- Port: Source Port. With this option, the farm will assign the same backend for each incoming connection depending on the source port only.
- MAC: Source MAC. With this option, the farm will assign the same backend for each incoming connection depending on the link-layer MAC address of the packet.
- Source IP and Source Port. With this option, the farm will assign the same backend for each incoming connection depending on both, source IP and source port.
- Source IP and Destination Port. With this option, the farm will assign the same backend for each incoming connection depending on both, source IP and destination port.
Farmguardian
L4xNAT farms lack built-in health checks for backends, making it necessary to configure Farmguardian for this virtual service.
You can assign either the default or personalized advanced health checks to this service from any existing farmguardian check.
For further information about Farmguardian, go to the Monitoring >> Farmguardian section.
Notice that after selecting the farmguardian, it will be automatically applied to the farm.
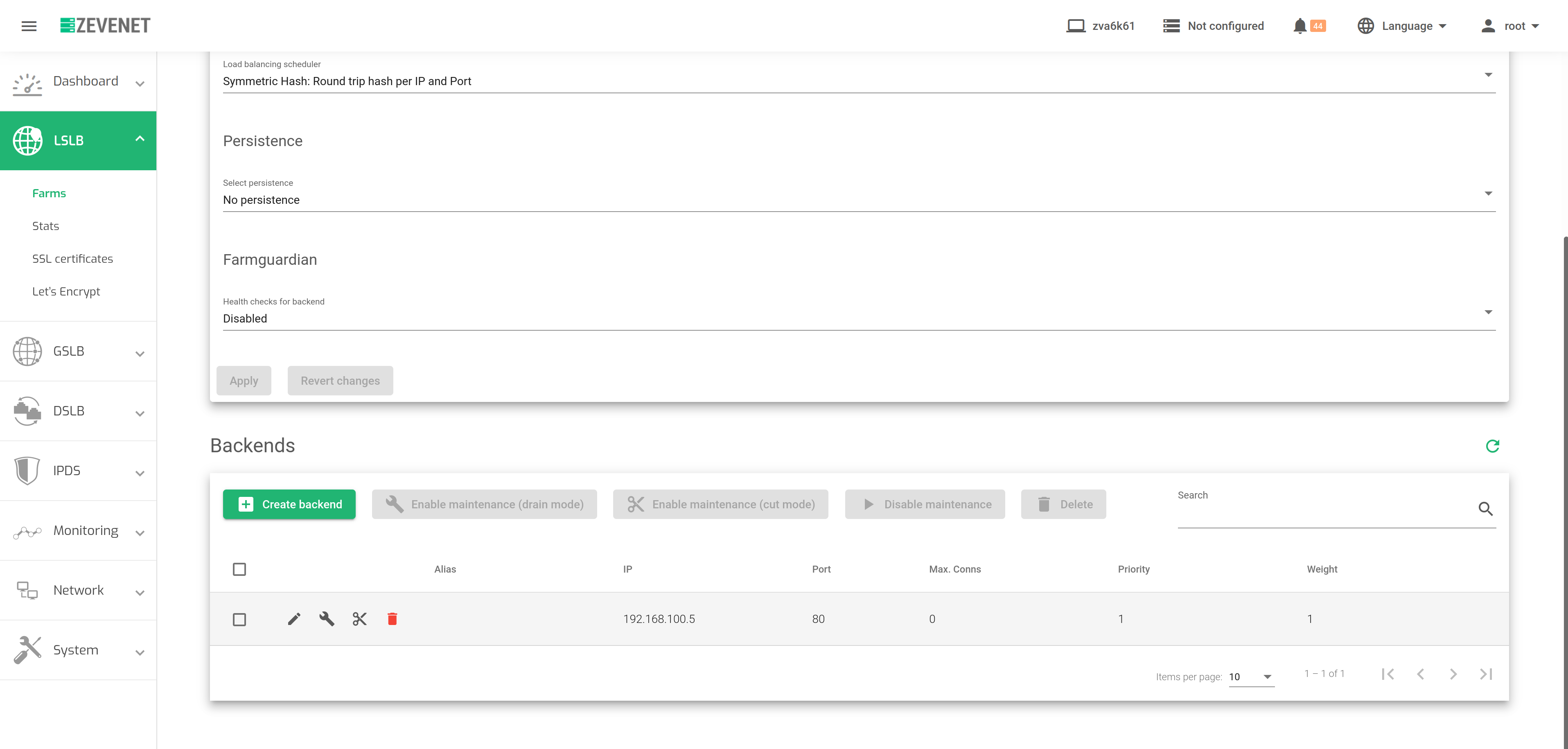
Backends
In this section, you will be able to modify the configurations of backends or add new ones to a given farm.
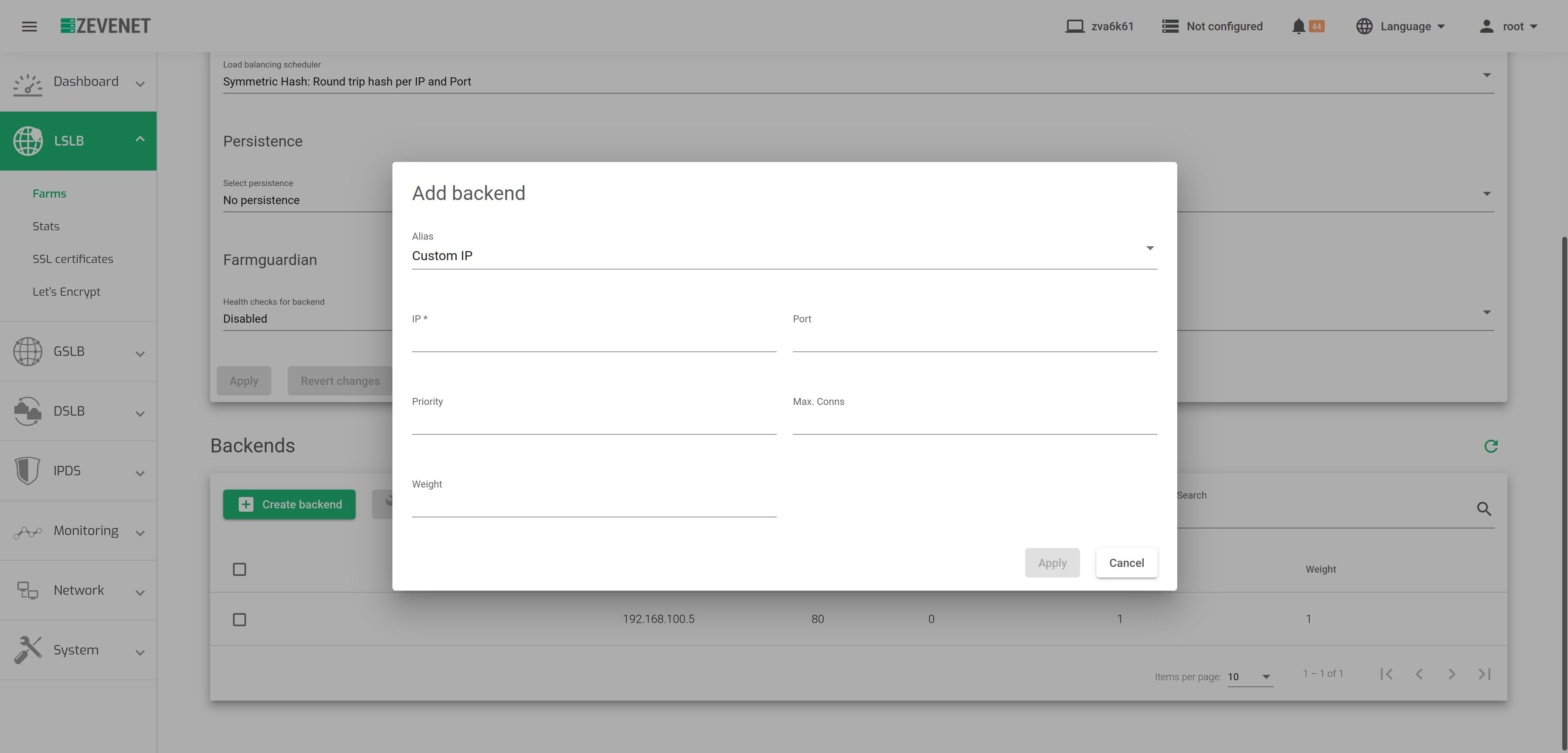
Create backend. This button will show the Add backend form when clicked. The configurations are meant to add a new backend to a given farm.
- Alias. This field shows the drop-down list with all the available backend aliases.
- IP. The Network-Layer IP Address to be used when forwarding traffic to the backend.
- Port. The Port to be used when forwarding traffic to the backend.
- Priority. The priority value for the current real server. Lower values have higher priority. The default service priority value is 1. When a backend fails, the service priority will be increased by 1. When the backend goes live again, the service priority value will be decreased by 1. Active backends contain priority values less than or equal to the service priority.
- Max. Conns. The number of connections that will be allowed to connect to the backend. If the limit is reached, the new connections will be discarded.
- Weight. The backend weight for traffic balancing when the weight algorithm is set. This weight determines how preferable the backend is against other backends. This field allows integer values higher than or equal to 1 (lowest value).
Bulk actions. On the right of ADD BACKEND, you will see the following actions which could be performed for one or more backends at the same time.
Actions: These are the actions for configuring the backends.
- Enable Maintenance. This action is available if the backend is up. It puts a real backend server in maintenance mode. Therefore, no new connections will be redirected to it. There are two methods for enabling the maintenance mode:
- Drain Mode. Keeps the established connections and persistence if enabled, but will not accept new connections.
- Cut Mode. Directly drops all active connections against the backend, closing any connection between the backend and clients
- Edit. Opens the edit form, the same as the add form, to change any backend value.
- Disable Maintenance. This action is only available if the backend is in maintenance mode. It will enable new connections to be forwarded to the backend server again.
- Delete. Remove the backend server of the virtual service. If the backend has an alias, the alias won’t be deleted.
Backends. This table shows all the backends already configured on the farm.
- Alias. A backend Alias if one alias has been previously defined for the backend.
- IP. The IP address of the backend where the connections will be forwarded.
- Port. The port where the connections will be redirected to at the backend. If a blank space or an asterisk‘*’ is set, connections will be redirected to the same port that was received.
- Priority. The priority value for the backend server. The accepted value is an integer higher or equal to 1. A lesser value indicates higher priority to the current real server. By default, a priority value of 1 will be set.
- Weight. The weight value for the current real server. A higher value indicates more connections delivered to the current backend. By default, a weight value of 1 will be set.
- Max. Conns. This value will be the maximum number of flows or established connections to a certain backend. If the limit of clients connected to a given backend is reached, the backend will not accept more traffic. The client will reconnect to another suitable backend. The default value is 0, which means unlimited.
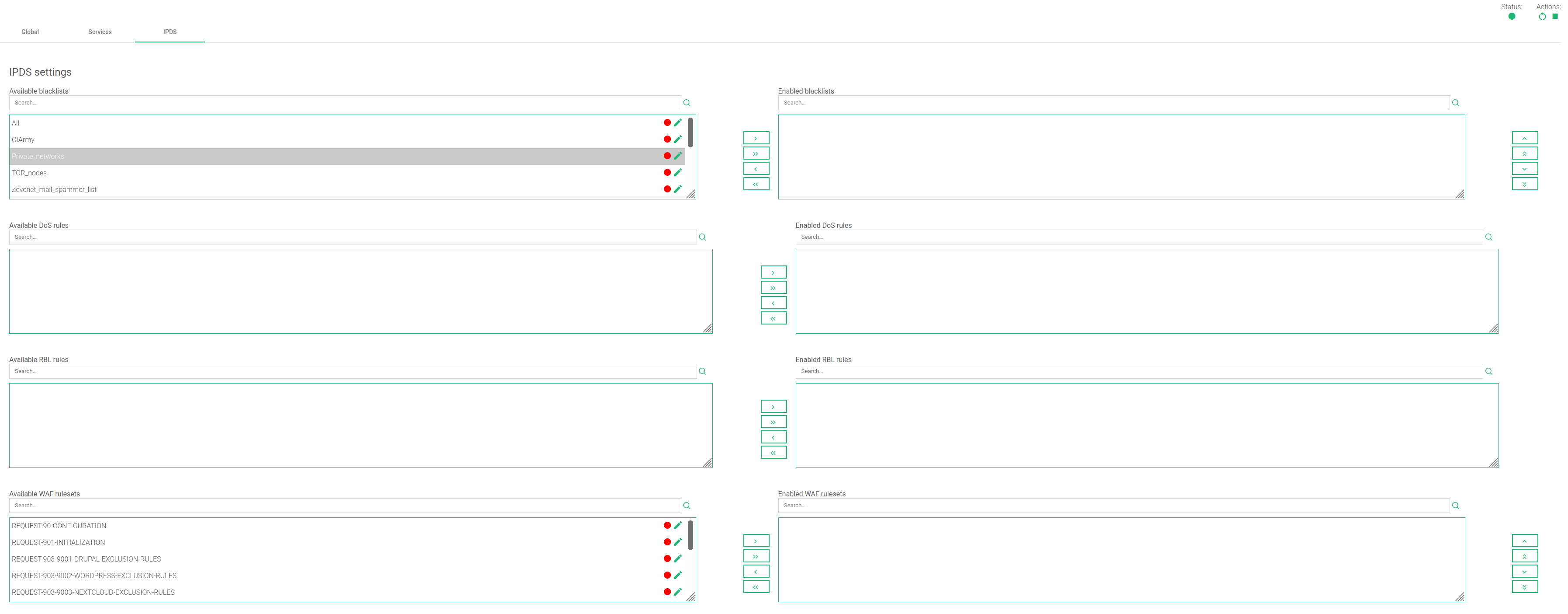
IPDS Rules for L4xNAT farms
This section let you enable IPDS rules. The list shows different types of protection and a select box to enable them. For further information please go to the IPDS >> Blacklists rules, IPDS >> DoS rules, IPDS >> RBL rules or IPDS >> WAF rules specific documentation.
For each of the four types of IPDS rules, Blacklist, DoS, WAF, and RBL, there are two tables, Available and enabled. There is also a chain icon. Under the Available table, you will see that all the available rules are of the same kind, and can be applied to a given farm. Regarding the enabled table, you will see that the rules applied to the selected farm are of the same type. There is also a status symbol for each rule which tells if the rule is stopped (red color) color or if it is running (green color).
Each rule can be accessed by clicking on the edit icon which will allow you to change rule parameters or even start/stop the rule. You will not be able to create a new rule inside this farm view. Change it through the IPDS section.
Add a rule by clicking on the desired rule followed by clicking on the right single arrow. Or, you can select more than one by simultaneously keying the shift key and selecting the rules that you want to add. You will then click the right single arrow. You can also add all the available blacklists by clicking on the right double arrow.
To delete one or more rules, select them and click on the left arrow or click on the double arrow to remove all.