The Web Application Firewall, WAF, is the tool to detect and to block malicious HTTP traffic that is going across the HTTP(S) farms. WAF works searching and analyzing patterns with the purpose of applying advanced security policies. Those rules are grouped in set rules and they have to be applied to HTTP farms. The WAF rules will be checked after decrypting SSL packets, then, it is possible to apply patterns again the HTTP body in an SSL traffic.
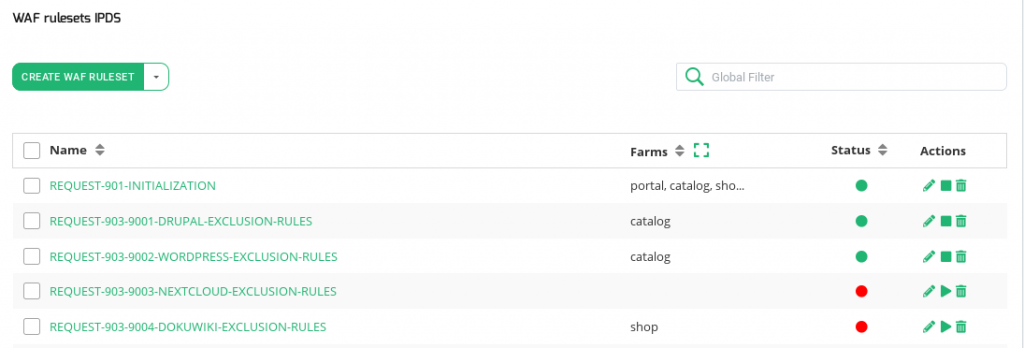
In the WAF rulesets view is shown an overview of the available rule sets:
NAME. Rule set name identification, it is a descriptive name about the kind of rules that the set contains. Click on it to enter to the editing form.
FARMS. The Farms to which the rule is applied. This field may be expanded using the small icon (little arrows) at the right side of the FARMS column header. By default is limited to 20 characters. If the list of farms is longer it is possible some of them are hidden. Use that small icon to expand the view.
STATUS. Rule set status is represented by the following status color codes:
- Green: Means ENABLED. The rule set is actually being checked for the farms are using it.
- Red: Means DISABLED. The rule set is not enabled, thus it is not having any effect on the farm.
ACTIONS. Allowed actions for the status of the WAF rules:
- Edit. To modify the rule set settings or assign a farm service if needed.
- Delete. Remove a rule set.
- Enable. To enable the WAF set for all farms where it is applied.
- Disable. To deactivate the WAF set for all farms where it is applied.