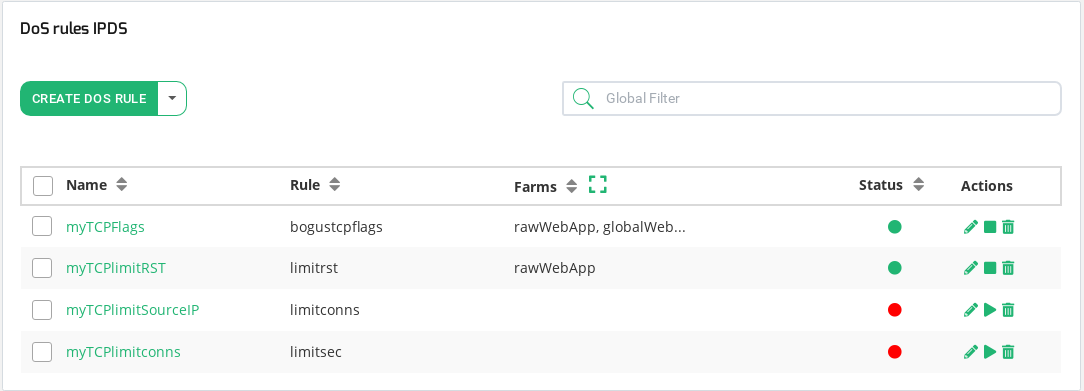
The DoS or Denial of Service section within the IPDS module permits to configure and set protection rules at System or Farm service level.
The System rules are preloaded but the Farm rules should be configured by the administrator. This section shows the available lists:
Name. Rule name identification. Click on it to enter the editing form.
Rule. It’s the type of rule. The different options will be:
- Connection limit per second. Protect the farm service limiting the number of connections per second accessing to the service.
- Total connections limit per source IP. Protect the farm service limiting the number of connections per source IP access to the service.
- Check bogus TCP flags. Protect the farm service from bogus TCP flags packets.
- Limit RST request per second. Protect the farm service of RST requests for TCP connections by limiting the RST packets per seconds accepted.
Farms. The Farms to which the rule is applied. This field may be expanded using the small square icon at the right side of the Farms column header. By default is limited to 20 characters. If the list of farms is longer it is possible some of them are hidden. Use that small square icon to expand the view.
Status. Rules status are represented by the following status color codes:
- Green: Means ENABLED. The rule is actually being used.
- Red: Means DISABLED. The rule is not enabled, thus it is not having any effect on the farm.
Actions. Allowed actions for DoS rules:
- Edit. To modify the rule global settings or assign a farm service if needed.
- Delete. Remove a created farm service rule.
- Start. To activate a system rule.
- Stop. To deactivate a system rule.
Bulk actions submenu. Allowed actions for one or more DoS rules are:
- CREATE DOS RULE. Create a new rule to be assigned to certain farm services.
- DELETE. Remove a created farm service rule.
- START. To activate a system rule.
- STOP. To deactivate a system rule.
Check out the video tutorial about DoS and test case.
Next step, create a custom DoS rule.