Overview
KRACK attacks are a WPA2 series of vulnerabilities that permits to an attacker to take advantage of a wireless connection to decrypt and hijack the wireless communications where the underlying data could be exposed. All devices using WPA1 and WPA2 are affected and, for mobile devices with Android 6.0 are even more easily to take advantage of this vulnerability.
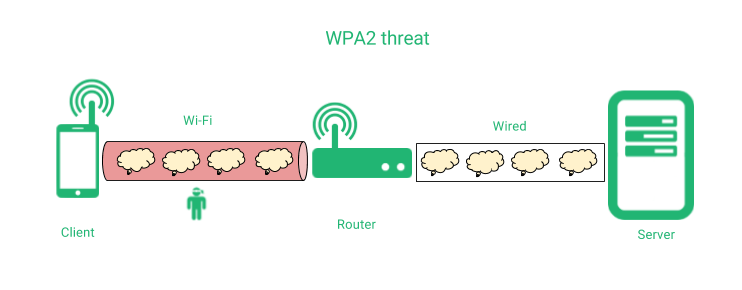
WPA2 is a network protocol that provides authentication and encryption at network layer, but the lack of forward secrecy allows to anyone that discovers the master passphrase can read all the data through a given Wi-Fi networks, PPP, VPN or any other network encapsulation using WPA, as it’s shown below.
A man in the middle could hijack the connection by reinjecting packets during the communication handshake that is done during the initialization of the connection, and apply HTTP virus, randsomware injection or any other malicious content through the communication.
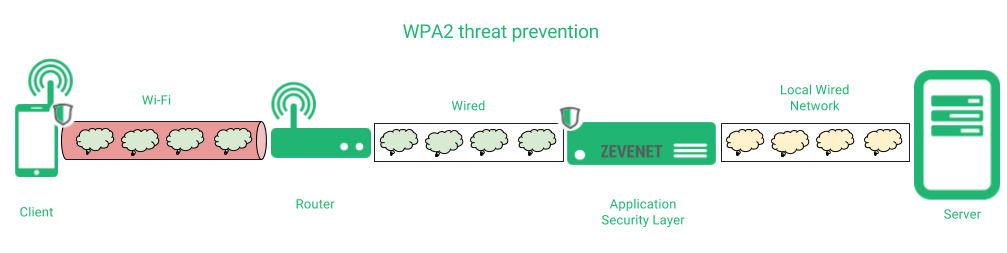
In order to prevent any data disclosing due to such vulnerability, we recommend to include an Application Security Layer protection that ensures a security channel point to point between the client and the application server, regardless if the network layer is encrypted or not, as it’s shown below.
In this case, we propose the use of an Application Security Layer that ensures that all the data between the client and Zevenet is fully protected, so the attacker can’t disclose any data although the wireless connection is hijacked. Finally, the connection between Zevenet and the real application server could be in plain or encrypted, depending on the network architecture.
The recommendations to protect your communication data are:
1. Build a Transport Layer Security by default for your applications and servers, for example with an Application Security device which, in addition, provides of Load Balancing and High Availability capabilities like Zevenet. That option implements the communication through protocols like HTTPS, SSH, SFTP, SMTPS, IMAPS, etc. instead of their plain protocol brothers. Zevenet also allows an easy management of certificates for such services.
2. Keep an up to date Application Security Layer with the security patches and advisories that are provided through any of the Support Services available. In addition, tools to detect and fix weak ciphers and configurations are provided to maintain the services with the high levels of security.
3. Implementing an Application Security Layer allows to hide and masquerade all the open ports, networks or services that shouldn’t be published through Internet and the possibility to enable the Intrusion Prevention and Detection System module that protects all your services against DoS attacks, TCP flooding, malicious hosts and the most common attacks.
Try Zevenet or contact us for more information.