IPDS RBL Domains
Those domains are internet servers with the purpose of maintaining a list of bad reputation IP addresses. A server IP address get into this list when the systems detect a bad use of the network. Spammers, force brute attackers etc. compound the mayority of those lists.
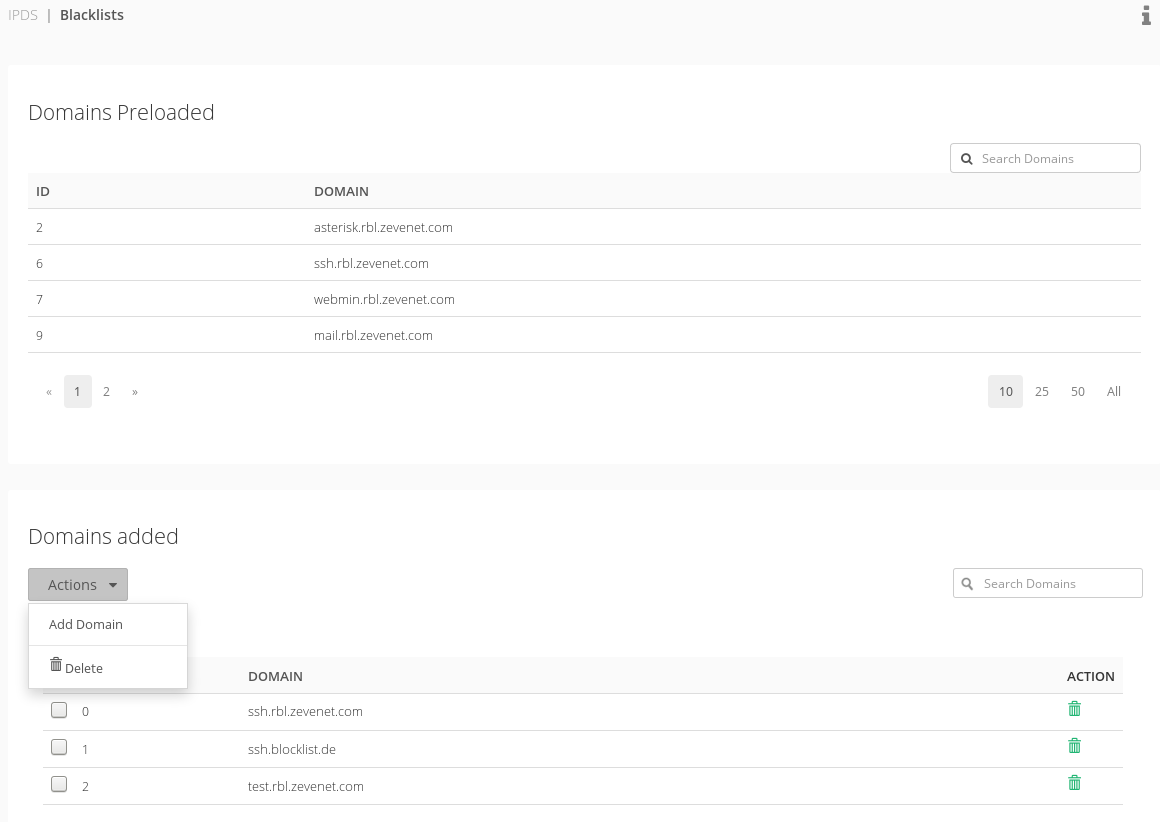
In this section you could add or remove your custom domains. If your company have an DNS with an up to date custom list of dangerous, forbidden or what ever reason list of IP addresses that you desire to block, this is the section where to use it.
The first section shows the preloaded domains which are maintained and updated by Zevenet. If one of the zevenet domains is used, your load balancer will query them in first place. Zevenet DNS for RBL rules are ns1.rbl.zevenet.com and ns2.rbl.zevenet.com. Please, be sure that those DNS are reachable from your Zevenet Load Balancer.
As mentioned, for this to work it is needed that your Zevenet Load Balancer has connectivity to Zevenet DNS. If the Load Balancer is under a Firewall this could be achieve by opening the 53 UDP Port.
This direct queries to Zevenet DNS increases system performance. If Zevenet dns are not used, normaly the query is done against a different DNS (for example 8.8.8.8) which later will resend the query to the final DNSBL server (for example blocklist.de)
For this purpose, the afore mentioned increase in performance, Zevenet keeps a mirror of DNSBL from blocklist.de The mirror is updated in a daily basis.
Domains added section allows you to add your custom domain. Each domains added should be a DNSBL (domain name server block list).
DNSBL queries
When a mail server receives a connection from a client, and wishes to check that client against a DNSRBL, also konw as DNSBL (let’s say, sbl.spamhaus.org), it does more or less the following:
- 1 – Take the client’s IP address—say, 172.168.42.23—and reverse the order of octets, yielding 23.42.168.172.
- 2 – Append the DNSBL’s domain name: 23.42.168.172.sbl.spamhaus.org.
- 3 – Look up this name in the DNS as a domain name (“A” record). This will return either an address, indicating that the client is listed; or an “NXDOMAIN” (“No such domain”) code, indicating that the client is not.
Optionally, if the client is listed, look up the name as a text record (“TXT” record). Most DNSBLs publish information about why a client is listed as TXT records.
Looking up an address in a DNSBL is thus similar to looking it up in reverse-DNS. The differences are that a DNSBL lookup uses the “A” rather than “PTR” record type, and uses a forward domain (such as dnsbl.example.net above) rather than the special reverse domain in-addr.arpa.